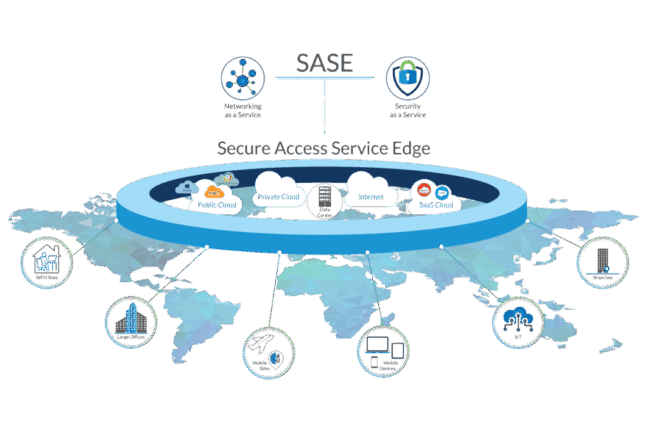
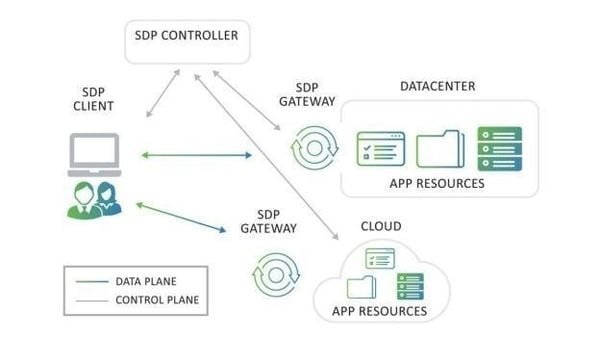
SASE
(Secure Access Service Edge) Converges network and security services, but still routes traffic through cloud edges that remain exposed to scanning, reconnaissance, zero-days and attackable.
Prevent-First removes the discoverability entirely – thus no exposure.